The Open Systems Interconnection (OSI) model describes how data communications should take place. When protocols or other standards are developed, they are placed into a layer of the model, which helps communication protocol integration and conceptual understanding.
This is why it is important as an IT professional to understand the aspects of the OSI model as it provides the fundamental concepts of communications between systems and applications.
It's Layers all the way down
The OSI model, published by the International Standard Organisation (ISO) in 1984, relates to connecting systems that are open for communication with other systems. It does this by categorizing the network communication into seven abstract layers, grouping similar functions into the same layer. The model is more than 3 decades old, but the fact that it is still relevant proves the power of its concepts.
The OSI model defines standards for:
- How devices communicate between each other
- The means used to inform devices when and when not to send data
- The methods which ensure that devices have a correct data flow rate
- The means used to ensure that data is passed to, and received by the intended recipient
- The manner in which physical transmission media is arranged and connected.
7 layers to rule them all
The OSI model divides the network communication into a vertical stack that consists of the seven layers that are depicted in the figure below:
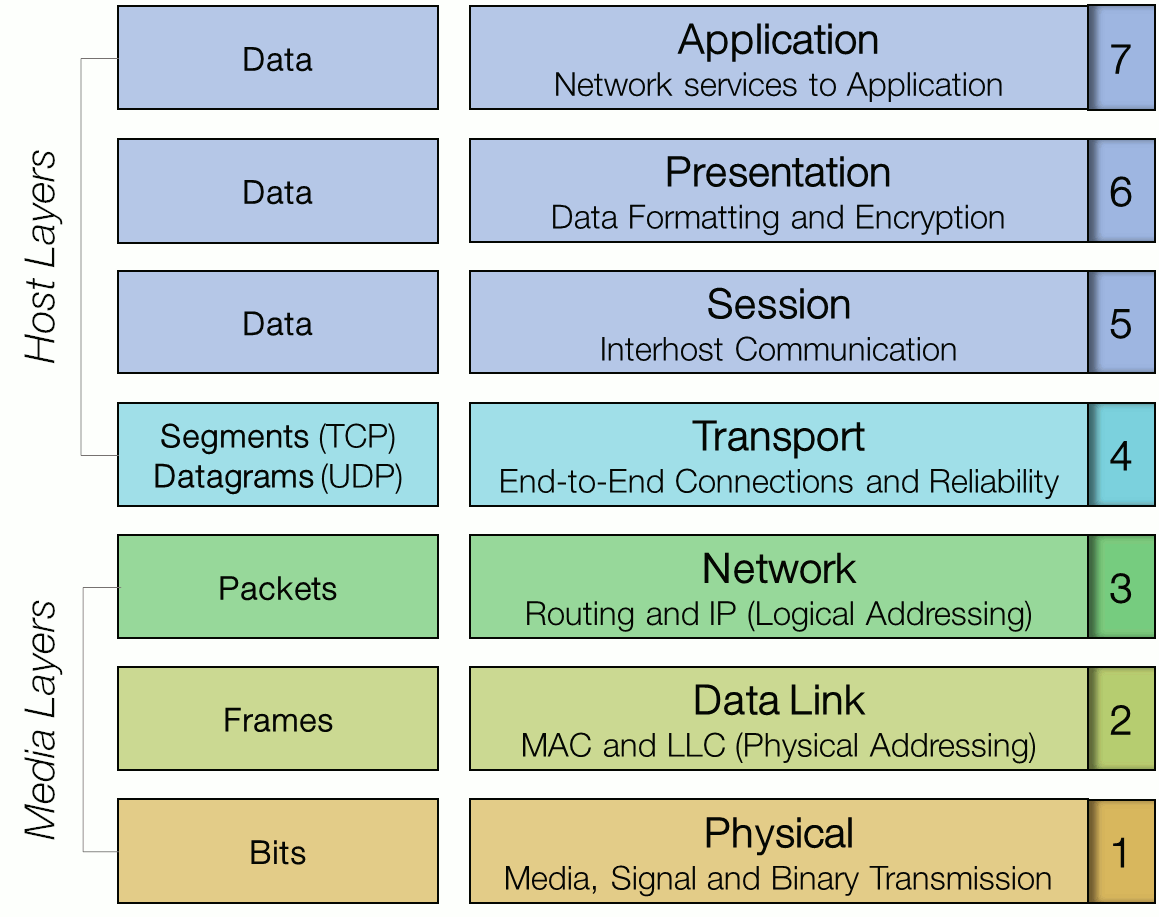
Each layer takes care of a specific job and is intended to function with the layer above and the layer below. A summary of each layer's responsibilities:
-
- Application - High-level API's, including resource sharing, remote file access
-
- Presentation - Translation of data between a networking service and an application. This is the layer where character encoding, data compression and encryption takes place.
-
- Session - Managing communication sessions.
-
- Transport - Reliable transmission of data segments between nodes on a network, including segmentation, acknowledgment and multiplexing.
-
- Network - Structuring and managing a multi-node network, including addressing, routing and traffic control.
-
- Data Link - Reliable transmission of data frames between two nodes connected by the physical layer.
-
- Physical - Transmission and reception of raw bit streams over a physical medium.
The top 4 layers are called the Host layers and the bottom 3 layers are referred to as the Media layers. The following chapters will describe these layers in more detail.
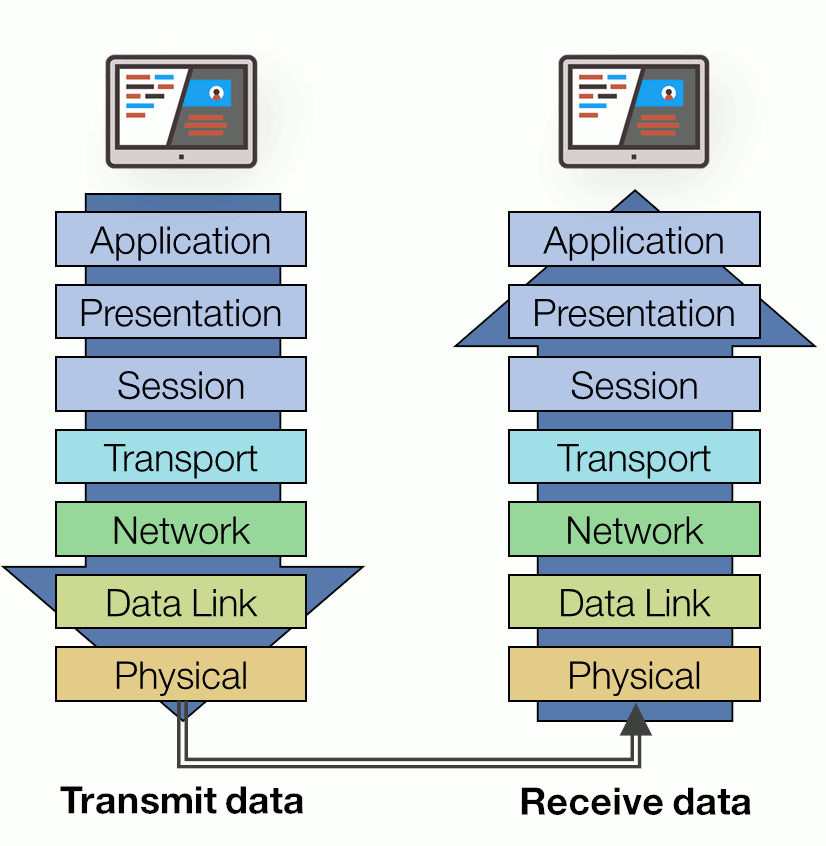
In the OSI model, control is passed from one layer to the next. When transmitting data from one machine to another, the data flow starts at the Application layer proceeding down to the Physical layer. Then over the channel to the receiving machine and back up the hierarchy.
Layer 7: Application
High-level API's, including resource sharing, remote file access
The Application layer is the highest layer of the OSI model. It provides the interface between the network protocol and the software running on the computer. The Application layer is the location where users and application processes access network services.
Some commonly needed functions are provided at this layer:
- Resource sharing
- Remote file access
- Remote printer access
- Network management
- Directory services
- Electronic messaging
- Network virtual terminals
- etc.
Application layer - protocols
Common application protocols that work in this layer include: HTTP, FTP, SMTP, DNS, Telnet, SSH, IMAP, POP, SNMP, etc.
Layer 6: Presentation
Data Formatting, encoding, compression and encryption
The Presentation layer's primary responsibility is to define how the data is communicated by the network hosts.
When transmitting data from the sender to the receiver, the application of the sender moves the data to the Presentation layer. This layer then translates the data to a common format which can be read by both computers. On the receiving end, the Presentation layer translates the data to a format which the application can read.
Compression, encryption, serialization, protocol conversion, character set conversion all fall in the functions of this layer.
Presentation layer - protocols
Common examples for protocols and technology that operate in the Presentation layer include X.25, ZIP, XML, JSON, ASCII, EBCDIC, JPEG, MP3, etc.
Layer 5: Session
Managing communication sessions
The Session Layer provides process to process communications between two or more networked hosts. This layer is responsible for maintaining proper communication by establishing, managing and terminating sessions (a property of TCP) between two nodes. It takes care of gracefully closing sessions and for session check pointing and recovery.
The following important functions are performed at this layer to establish, maintain and terminate communication sessions between applications:
- Name lookup and security functions (authentication, authorization)
- Placement of header information in a packet which determines the point where a message starts and where it ends.
- Data synchronization. The layer performs synchronization between the Session layer of the data sender and the Session layer of the receiver of the data.
- Controls whether the data being exchanged in a session are transmitted as full or half duplex messages.
Session layer - protocols
NetBIOS, RPC, SOCKS, L2TP, SDP, H.245, NFS, etc.
Layer 4: Transport
End-to-end connections and reliability
The Transport Layer ensures that messages are delivered error-free, in sequence and with no loss or duplication. This layer verifies that the application transmitting the data is actually allowed to access the network and verifies that both ends of the connection can start the data transfer process.
The following important functions are performed at the Transport layer:
- Same order delivery
- Guaranteed data delivery (reliability)
- Flow control
- Error detection
- Error recovery
The common Transport protocols utilized at this layer are:
- User Datagram Protocol (UDP): UDP is a connectionless protocol that does not provide reliable data transport. No acknowledgments are transmitted. This protocol gives a higher throughput and shorter latency and is often used for multicasting, broadcasting and real-time multimedia communication where occasional packet loss is acceptable. Messages sent with UDP are referred to as datagrams.
- Transmission Control Protocol (TCP). TCP is a connection-orientated protocol that offers greater reliability when it comes to transporting data than what UDP provides. With TCP, the application which sends the data receives acknowledgment or verification that the data was actually received. It is used for many protocols, including HTTP web browsing and email transfer where lossless data transfer is important. Individual units of data transmission in the TCP protocol are referred to as segments. See also my article on TCP 3-way handshake and port scanning.
Transport layer - protocols
Besides TCP and UDP, some common protocols that operating in the Transport layer include SPX, SCTP, RDP and DCCP.
Layer 3: Network
Routing, addressing and traffic control
The network (or Internet) layer is primarily responsible for establishing the paths used for transfer of data packets between nodes on the network. This is the layer that routers operate on.
The functions performed at the Network layer are:
- Addressing, logical network addresses and services addresses
- Routing functions, route discovery and route selection
- Packet switching
- Packet sequence control
- End-to-end error detection
- Congestion control
- Network layer flow control and Network layer error control
- Gateway services
This layer determines via which path data should be sent and does this based on the following:
- Network conditions
- Priority of service
- Other factors like traffic control, routing and frame fragmentation and reassembly.
The network layer also takes care of mapping logical (IP) addresses to physical (MAC) addresses that are used in the Data Link layer.
If the message is too large to be transmitted from one node to another on the data link layer, the message may be split into several fragments at the network layer on one node. These fragments are sent independently and reassembled at the receiving node. It may, but does not need to, report delivery errors.
The Internet Protocol (IP) operates in this layer.
Network layer - protocols
Besides IP, the following common protocols are included in the Network layer: ICMP, IPsec, IPX, DDP, CLNP, etc.
Layer 2: Data Link
Reliable transmission of data frames between two nodes connected by a physical layer
At the Data Link layer, data packets are encoded into bits. It defines the protocol for flow control and to establish and terminate a connection between two physically connected nodes on the network.
It handles errors in the physical layer and is concerned with local delivery of frames between devices on the same LAN. Data-link frames, as these protocol data units are called, do not cross the boundaries of a local network. Inter-network routing and global addressing are functions provided by higher layers. This allows the data-link protocols to focus on local deliver, addressing and media arbitration.
The IEEE 802 is a family of standards dealing with Local and Metropolitan area networks and divides the Data link layer into two sub layers:
- Logical link control (LLC) layer – provides addressing and control of the data link. It handles error checking, flow control and frame synchronization.
- Medium access control (MAC) layer – controls how a node on the network gains access to the medium and permission to transmit to it.
Most network technologies based on IEEE 802 use MAC addresses that are used in the MAC-layer for addressing purposes.
Data Link Layer - protocols
Protocols in this layer include Ethernet, ARP, PPP, Token ring, StarLAN, NDP, L2TP, etc.
Layer 1: Physical
Hardware, signaling and binary transmission
The physical layer is the lowest layer of the OSI model and consists of the functionality that interacts with the actual hardware and signaling mechanism.
It handles the transmission and reception of the unstructured raw bit stream over a physical medium and carries the signals for all of the higher layers. Think of the wiring, cabling, frequencies, pulses used to represent binary signals, etc.
The physical layer provides:
- Data encoding: converting 1s and 0s into characteristics of the physical medium. It determines what signal state represents a binary 1, how the receiving station knows when "bit-time" starts and how the receiving station delimits a frame.
- Physical medium attachment. For example: how many pins do the connectors have and what is each pin used for?
- Transmission technique: determines whether the encoded bits will be transmitted by baseband (digital) or broadband (analog) signaling.
- Physical medium transmission: transmits bits as electrical or optical signals appropriate for the physical medium. This determines what physical medium options can be used and how many volts/db should be used to represent a given signal state, using a given physical medium
Physical Layer - protocols
Technologies in this layer include Infrared, ISDN, DSL, Bluetooth physical layer, CAN bus, USB physical layer, Ethernet physical layer, IEEE 1394, RS-232, etc.
